Hackers are always finding ways to penetrate in to your systems and applications. This can have major impact on the company’s business and reputation.
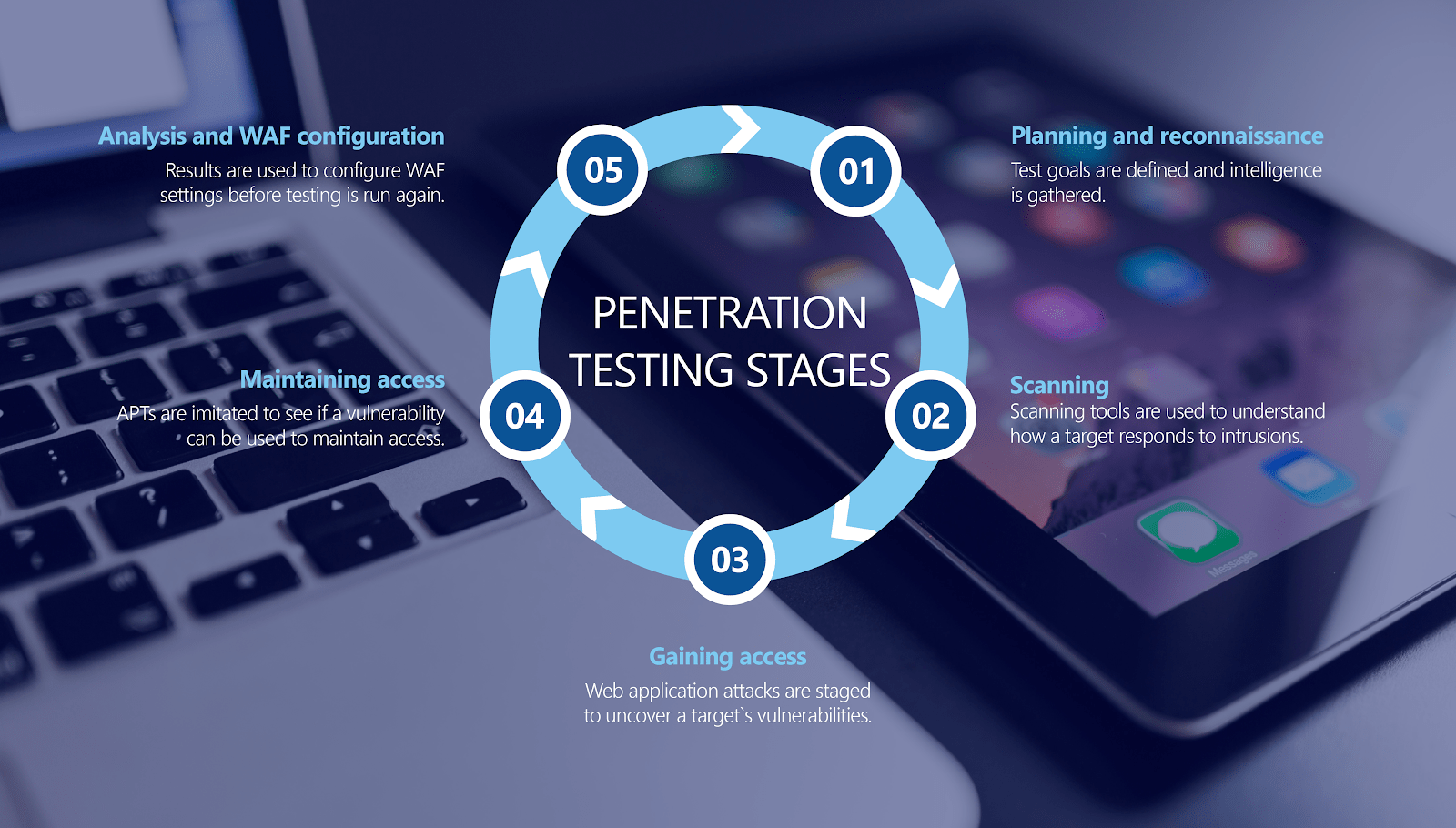
Penetration testing is not just about discovering flaws in the system and furnishing a report for us. People mostly mix the terms vulnerability assessment and penetration testing, while vulnerability assessment only scans and identify weaknesses in the systems, penetration testing uses those weaknesses to hack into those systems.
Our penetration testers will work with you to tailor the project scope, which will define which systems and networks to emphasize on. Our expert team will exploit the vulnerabilities which could affect your overall business and help you out in coming up with effective solutions. The main objective of our practitioners is to penetrate into your systems and find loopholes all possible means that an actual hacker might do and then fix those loopholes.
Penetration testing mimics the same procedures and strategies that malicious hackers use to invade into your systems, applications and networks. It is the most exhaustive way to find out the vulnerabilities as it replicates all those ways which an actual hacker uses to attack, only this time you know who is doing it
If you think about it in a simple way, penetration testing is like paying a security agent to see if he or she can break into your house and then tell you in detail how he or she did it. This way you would know exactly which parts of your house are safe and which parts are unprotected.
It is significant to understand that one pen test cannot make your systems safe forever, as technology changes every day, new vulnerabilities arise in existing systems. To have thorough security one requires persistent vigilance, which is why we focus on building long term relationships with our clients and not just providing you with a checklist of vulnerabilities but guarantee the best possible pen test which offers you a proficient, high end security audit customized according to your needs.